- October 22, 2018
TSCM (Technical Surveillance Countermeasures)
Written by Darren L. Epstein, all rights reserved. Copyright © 2019 / (DO NOT COPY)
Spying might make you think of James Bond movies or the CIA… however many don’t realize, it’s become a larger part of the corporate industry and private sector. Companies of all types are currently spying on each other…not always to steal trade secrets, sometimes to just gain a competitive edge. Corporate espionage can not only be a security issue, but a grave corporate killer, if not addressed! You may not see yourself as a target, but if you’re perceived as wealthy or a person of interest, ‘someone’ (competitor, disgruntled lover, an ambitious employee, etc.) will make you a target. Without providing protection against a possible threat, you might find that new idea or invention now part of a competitor’s product line. If you’re a person of importance, or happen to work with sensitive items, someone might also try to blackmail you.
Within this article, I’ll discuss the various methods used for eavesdropping and what equipment and services are needed to conduct a thorough TSCM Sweep. When hiring a TSCM company, make sure they follow basic TSCM protocols.
- Conduct a Thorough Physical Search.
- UV Light Sweep looking at vents, AC receptacles, etc. Once completed, mark areas.
- An Audio Spectrum Analyzing Search of the low Hz and high GHz range.
- A Thermal Imaging Sweep looking for heat signatures within walls and/or furniture.
- Telephone PBX and Physical Lines Analyzed / Time Domain Reflectometry
- Inspection of computers and LAN connections.
- Inspection of printers and computer output devices.
- VLF, microwave and ultrasonic detection.
- Non-Linear Junction Detector searching for remote bugs turned off.
- X-ray items if necessary.
- Oscilloscope survey to observe the changes of an electrical signal over time.
- Install Transducers; audio jamming devices (acoustic white noise generators).
*Mobile phones, computers, Alexia/Google Devices, TVs, Gaming Systems, etc. are COMPUTERS, these require ‘COMPUTER FORENSICS’, a different type of specialist.
There has always been a need for spying…the ‘need to know’ what someone else was doing is a basic human trait. The sophistication of eavesdropping has changed dramatically… as we move away from the ‘cup against the wall’ and towards laser listening devices and high spectrum frequency hopping, the basics and principles still remain. First off, you might be asking yourself…what does TSCM mean? If you’re searching for a company to conduct a debugging or were researching the topic, you most likely came across the term, TSCM. Technical Surveillance Counter Measures (TSCM) is the science of looking for eavesdropping equipment. On the other hand, a technical surveillance device (TSD) is an item designed to intercept communication or conversations, more commonly known as bugs. There are many countries that illegally import eavesdropping and bugging equipment into the United States, such as France, Germany, Lebanon, Italy, Canada, Israeli, England, Japan, Taiwan, South Africa…etc.
The U.S. Department of State (referenced in 1997) estimates 6,550 corporate eavesdropping incidents take place each year and approximately 888 million dollars of illegal eavesdropping equipment is imported into the United States each year. Compared to the losses… it’s unconceivable, costing corporate America closer to 800+ billion per year! The FBI and other federal law enforcement agencies have openly stated they lack the resources and training to enforce and investigate technical countermeasures (bugging).
Eavesdropping equipment can be hardwired or wireless, most commonly radio frequency (Hz, Mhz, Ghz, etc.). Eavesdropping can be conducted by leaving a device behind to gain Intel, however many newer devices can be remotely activated. Listening devices can also be hidden or disguised within ordinary products, making them difficult to locate, e.g. alarm clocks, smoke detectors, etc. Depending on the sophistication, some culprits will use existing devices and/or technology to listen in and gather Intel, e.g. (Telephone Wiring, Cellular GSM, Cable TV, Wi-Fi, Bluetooth, and even AC circuitry). Today with phones and TV’s acting more like computers… you also have to search for computer viruses. A well-planned virus could turn your laptop mic/webcam into a listening device or turn your mobile phone into a power mic. You could enter a boardroom without knowing your mobile phone was sharing trade secrets with a competitor. Knowledge is POWER, be informed so you’re protected!
If you are concerned about eavesdropping taking place, I implore you to take it seriously and contact our offices or a TSCM specialist you trust and have vetted. NOT FROM THE LOCATION IN QUESTION! Do not call from your cellular phone, it could have been compromised! If you decide to walk into our office, make sure you weren’t followed! If you purchased a new prepaid mobile phone with cash… feel free to call us but do it from a secure location! Not your car, it could have been compromised. Call us from a location with background noise (white noise), e.g. a busy mall, and walk as you are talking, don’t stay stationary; don’t be paranoid… but safe and smart!
Whoever you decide to use to conduct your TSCM, make sure the company retained is comprised of – knowledge, experience, and state of the art government grade equipment. TSCM Service is a science, you need a qualified technician searching the low Hz to high GHz ranges. There are numerous ways to eavesdrop and gather intelligence, below I list the most common attacks along with various equipment necessary to conduct a professional TSCM Sweep.
1. Microphone and tape recorder: The most common and easiest type of eavesdropping.
Very versatile… it can be worn, placed in a room, and even turned on remotely or by voice activation.
2. Transmitters (Bugs): The microphone or video picks up the communication transmits it as radio signals, i.e. 900 MHz, 2.4 GHz…etc. Some bugs are self-contained with microphone, transmitter and power supply. The sophistication ranges from simple intercom systems to professional government bugs. Since these devices are sending signals, we look to locate their spectrum waves; we do this by using a spectrum analyzer. Some bugs/transmitters are turned off and are turned on remotely, aka (remote bugs). This type of transmitter can defeat a spectrum analyzing sweep, as well as a thermal imaging sweep. If the remote bug is turned off, there wouldn’t be a signal sent to pick-up and detect, nor would there be much heat generated. Due to such, we suggest using a TSCM device that can locate transmitters turned off or hidden within walls. This type of TSCM device doesn’t search for signals or heat…but rather it locates ‘circuit boards’ and the mini magnets needed within these devices.
3. Through Wall Listening Devices: There is also equipment that can hear through walls, including brick walls; commonly used in situations with adjoining rooms (office, hotels, and apartments).
4. Laser Bounce Listening / IR Devices: This is or was a high-tech method for eavesdropping, however, with Internet and YouTube instructing others into how to build your own laser microphone, its become more accessible. The laser consists of an invisible infrared beam (RF), like your remote control when you increase the volume on your TV. The IR laser will bounce off a window and capture the audio within a room. It then sends the audio information back to the person who is conducting the eavesdropping. Professional laser listening devices can shoot a beam into a hotel room from another building nearby to intercept what’s being said. The technique of using a light beam to remotely record sound originated with Léon Theremin in 1947. When our agency conducts a TSCM Sweep (Technical Surveillance Countermeasures), we always search for laser listening devices and provide suggestions once the sweep is completed to keep your conversations secure.
TECHNICAL SURVEILLANCE COUNTERMEASURES 101
We conduct a three-part search looking for Hardwire (HW), Radio Frequency (RF), and Laser/Infrared bugs. The three-part search will consist of a physical search, telephone/phone lines, and spectrum/audio search. We use GSA and DOD certified equipment!
Hardwire: (Telephone, Telephone Line, and Carrier Current Search)
Listening devices that can be attached to your phone, telephone line, telephone system or even transmit your conversations over the AC power, via Carrier Current transmissions. These bugs are often powered by the line itself, so it pulls low amperage, making it difficult to detect. They can also be placed on your line outside, at the junction box, and professionals they can even tap into your lines miles away. Rest assured, we check your lines from your address to the telephone company central station. Our Time Domain Reflectometry equipment & spectrum analyzer sends signals through the line to the central office. We’re able to determine if your phones are being tapped from within your office or outside. Landline telephones produce amperage, aka (ohm) and our equipment will locate the amperage or ohm drain taking place and then locate the location of that drain. The AC wiring within your home or business can also transmit your conversations via Carrier Current. Right over the AC power wiring, rather than using a radio signal. The eavesdropper can listen from any point along the AC wiring until it goes through the electrical company’s next transformer. Rest assured, we also search A/C outlets and Carrier Current transmissions.
Mobile Cellular Phone: (Computer Forensics)
Searching a Mobile Phone for a listening device is more computer nerd then James Bond, the process is different. The mobile device is a computer, where computer forensics will determine if information is being sent out of your phone without your knowledge. We are basically looking for a virus that is transmitting your data to another email or IP address you aren’t aware of. Cellular Phone Debugging needs to be conducted by a trained computer forensic expert (we have on staff).
Radio Frequency (RF): (Spectrum & Audio Search)
Sends wireless signals throughout the air, any FM/AM radio or scanner device can intercept these signals. RF transmitters can be as small as a regular bug, but they need power to operate, often making them larger. RF Bugs can be battery or hardwired for power. They can be located within electrical outlets, A/C vents, ceiling tiles, under furniture, etc. A Physical Search helps, but you need a professional RF locater, also known as a spectrum analyzer. Cellular phones, portable phones, and various equipment send signals, we are looking for these signals. A top-quality spectrum analyzer searches the low Hz to high GHz frequency range.
GSM, TV, Wi-Fi, Bluetooth+ (Spectrum & Computer Signal Interception)
There are various new ways a culprit can gain access to your private information. They can strategically virus your Mobile Phone or TV to access the preinstalled camera and/or mic. Additionally, other forms of communication like Wi-Fi and/or Bluetooth are being used to hack your various devices, only to be turned against you.
IR Laser Listening Devices:
Often expensive, professional models are $25k+… but YouTube will teach you how to make a crude version. A laser (IR) “infrared” beam is shot into the room where observation is wanting to take place. The audio is transmitted back and decoded. The culprit shoots the IR invisible beam through a window or similar opening. Difficult to use for you need a direct line of sight.
NOTE: An operative could use an IR Listening Device and a RF transmitter… shooting the laser into a window while transmitting the data to a distant location, for the ultimate Intel and protection.
Physical search:
The removal of all electrical outlets, air vents, ceiling tiles, smoke detector covers, light switch covers…
OUR EXPERIENCE
- Technician is Department of Defense Classified Conference Sweeps
- United Nations Delegations — Sweeps of Mission Offices
- Federal Agency — Sweep of Federal Court Rooms Federal Commission — Examination of Critical Offices Embassies – Sweeps of Embassies in D.C.
- Governors – Audit of offices and Cabinet Member Homes
- Mayor’s Office and Comp Controller’s Office – Sweeps after 9/11
- Fortune 500 Companies
- Celebrities – High Profile Hollywood Celebrity Sweeps
- Sweep of Private Island Residences & Yachts
- Energy Company — Audit of Exec Offices, Aircraft & BOD meetings Oil Industry — Sweep of offices, residences and Learjet Wall Street — Audit of executive offices.
- Law Offices — Examination of offices during critical litigation.
- Religious Leader — Sweep of residence and office.
- Political Headquarters — Audit of strategy room & exec offices.
- Gaming — Audits of major corporate offices and residences.
- Media — Sweep of major executive broadcasting offices.
- Defense Contractor — Sweeps of management offices.
- Forbes List Elite — Sweeps for numerous EP organizations. Institute — Audit of executive offices.
Our TSCM technician has been a guest speaker for the TSCM Division of the
Federal Bureau of Investigation, The Espionage Research Institute and
American Society for Industrial Security.
Selecting a Qualified TSCM provider
- First, Verify the provider has attended a recognized TSCM academy. The ITC is the government school which is about 40 weeks long. The best private academy is REI located in Tennessee. Their courses are provided in modules, with the understanding the students have a communication electronics background. (Ask for copy of diplomas). The majority of vendors conducting TSCM have No formal training in the field.
- Second, Verify the provider has “real” TSCM equipment. State of the art detection equipment costs range from $100k to $300k plus! It’s NOT an inexpensive hobby. They should have: (1) OSCOR Blue Spectrum Analyzer, (2) TALAN Telephone Analyzer, (3) ORION Non-Linear Junction Detector, (4) FLIR Thermal Camera.
- Third, determine that the person providing the service conducts sweeps on a regular basis. Some firms conduct a few sweeps per year… you don’t need fancy equipment without a serious processional knowing how to use them.
OUR Technical Training:
Law Enforcement Technology Degree: Primary focus CSI, emphasis on forensic technology.
Certified Communication Electronics Technician: NRI Certified with FCC 1st Class Radio Technician & Microwave endorsement. Practical bench and field tech experience.
Facility Security Management: Department of Defense FSO certified in Information Security & Classified Information Management.
Communication Security Management: National Security Agency certified, COMSEC custodian.
| TSE-101 Technical Security Technology |
| TSE-201 Technical Surveillance Counter Measures |
| OBC-101 OSCOR Blue Advanced Spectrum Analysis |
| TCC-110 Telecommunication Analysis |
| DTC-210 Advanced Digital Telecommunications |
| ACE-320 Advanced TSCM |
| FLIR Infrared Analysis |
| RF Hawk Real Time Spectrum Analysis |
| SANS – VOIP Security |
TSCM Technology:
Frequencies of Interest:
(This will identify the majority of the bugs sold within Spy stores).
| Audio Detection | 300 Hz to 15 kHz Base Band Audio |
| Ultrasonic | 10 kHz to 150 kHz Ultrasonic Audio |
| VLF-Free Space | 20 kHz to 350 kHz Video Cameras & Tape recorders |
| Carrier Current | .3 kHz to 50 MHz 99% Voice (CC and PLA) |
| Carrier Current | 10 MHz to 450 MHz 99% Voice (AC Mains Antenna) |
| Free Space-HF | 3 kHz to 50 MHz 99% Voice |
| Free Space-VHF | 30 MHz to 300 MHz 10% Video/80% Voice/10% Data |
| Free Space-UHF | 300 MHz to 900 MHz 25% Video/60% Voice/15% Data |
| Free Space-MW1 | 900 MHz to 3.0 GHz 50% Video/40% Voice/10% Data |
| Free Space-MW2 | 3 GHz to 18.0 GHz Mostly Video and Data |
| Free Space-MW3 | 18 GHz to 26.5 GHz Mostly Video and Data |
| Free Space-MW4 | 26.5 GHz to 40.0 GHz (optional, based on threat) & UV Infrared! |
| 150 – 450 nm | Modulated UV Light Bugs |
| 350 – 700 nm | Modulated Visible Light Bugs (450 to 675nm very common) |
| 700 – 1100 nm | Audio Transmitters/Lasers (880 to 950nm very common) |
| 800 – 1510 nm | Audio Transmitters/Laser Microphones (rare) |
| 750 – 900 nm | Night Vision Illuminators |
| 850 – 1750 nm | IR Bugs & IR Illuminators & optical bugs installed in – (light bulbs, etc.) |
| 450 nm | Modulated Tungsten bugs |
| 490 nm | Modulated Sodium bugs |
| 575 nm | Modulated Fluorescent bugs |
| 50 – 750 kHz | Carrier Current Bugs (power, phone, HVAC lines) |
| 25 – 80 MHz | Ultra-low power devices (micro watt devices) |
| 65 – 130 MHz | Micro power Part 15 devices (FM broadcast band) |
| 130 – 150 MHz | Body Wires and Wireless Microphones – Band I |
| 150 – 174 MHz | Body Wires and Wireless Microphones – Band II |
| 174 – 225 MHz | Body Wires and Wireless Microphones – Band III |
| 295 – 310 MHz | Spread Spectrum and Micro Powered Bugs (micro watt devices) |
| 330 – 440 MHz | Audio/Video Bugs (398.605, 300.455, & 399.030 MHz are popular) |
| 430 – 550 MHz | Audio/Video Bugs (433.920 and 418 MHz is popular) |
| 800 – 990 MHz | Audio/Video Bugs (902-985 MHz ISM band is popular) |
| 1.10 – 1.95 GHz | Video and Audio (980 MHz to 1.45 GHz is very popular) |
| 2.00 – 2.75 GHz | Video and Audio (2.4 to 2.45 GHz is extremely popular) 5.60 – 7.50 GHz |
| 5.60 – 7.50 GHz | Video and Audio (5.8 to 6.2 GHz is becoming very popular) |
| 8.10 – 13.00 | GHz Video and Audio (Popular) |
| 850 – 950 nm | Infrared Transmitters |
| DC – 3 kHz | Typical Audio Band |
| 3 kHz – 500 kHz | Skin Effect (Non-Radiating) |
| 500 kHz – 3 MHz | Non-Radiating, Conducted RF |
| 3 MHz – 300 MHz | Conducted RF, Free Space Radiating |
| 300 MHz – 3 GHz | Free Space Radiating RF, Slightly Directional |
| 3 GHz – 22 GHz | Free Space, Low Attenuation, Highly Directional |
| 22 GHz | Water Vapor Absorption Band |
| 60 GHz – 3 THz | Limited Usage for Covert Surveillance |
World Class Technology

RADIO FREQUENCY SPECTRUM ANALYSIS is performed using the REI OSCOR Blue. The RF spectrum from 10 KHz to 24 GHz (as a minimum) is examined. Radio transmissions are captured and mapped to identify the presence of covert transmitters from within the protected area. (This analyzer will detect the latest burst, spread spectrum and frequency hopping devices, which is why federal intelligence agencies use the OSCOR Blue.)

DIFFERENTIAL RF ANALYSIS is performed using the Audiotel Delta V analyzer. Radio signals from 50 KHz to 5 GHz are processed using differential comparison techniques. (In metropolitan areas with high RF saturation, this detector pinpoints the transmitter source.)

CELLULAR TESTING is performed using the Blood Hound. Covert GSM transmitters are pinged using a proprietary technique to analyze up link utilization.
(The new era of surveillance technology is cell phone frequency bugs, which the majority of detectors will ignore.)
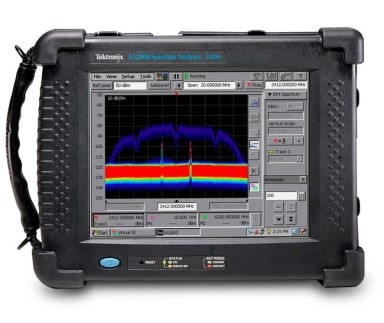
REAL TIME SPECTRUM ANALYSIS is performed using the RF Hawk. This analyzer covers 50 KHz to 6 GHz. (The DSP allows us to look inside conventional radio signals to detect covert transmitters broadcasting within legitimate carrier envelopes. It was specifically designed to identify, track and locate radio transmissions. Less than 2% of sweep firms have this technology.)

INFRARED THERMOGRAPHY is performed using the FLIR Scout to identify thermal signatures from covert devices. (Thermal signatures given off by covert surveillance devices and can be seen, when converted to visible light.)

NON-LINEAR JUNCTION DETECTION is performed using the REI ORION. High frequency RF signals are beamed into critical surface areas to illuminate covert electronic devices. (Virtually all surveillance technology uses electronic components, which are detected even if the device is switched off.)

ADVANCED TELEPHONE ANALYSIS is conducted using the REI TALAN. Comprehensive electrical measurements are taken on all line permutations for voltage, current, resistance, capacitance, audio paths, and line based RF signals. In addition, Frequency Domain Reflectometry is utilized to identify suspect connections on copper conductors. As a final test, NLJD is performed on all line pairs to detect unauthorized electronic devices.)

WI-FI ANALYSIS is performed using the Air Magnet LAN Analysis and Spectrum Analysis Software / Technology. Specific devices are mapped and analysis is performed on each signal encountered. (Many surveillance devices operate of Wi-Fi / Bluetooth Technology).

FIBEROPTIC INSPECTION is conducted using a variety of manual and electronic imaging techniques to examine areas which offered limited accessibility.
(Digital Voice Recorders and Covert Cameras are often hidden in HVAC ducts.)
World Class Technology
Defending your location once we depart

ANG2200 White Noise Generator Professional. This professional white noise generator defeats such listening devices as wired microphones buried in a wall, contact or spike microphones, transmitters located in AC outlets and laser/microwave reflection from windows.

REI’s TRN-2000 is a specially designed Transducer used to inject acoustic noise into walls, finished ceilings, windows, plumbing, and air ducts.

WMT-2000 Transducer Window Mount provides a safe method of attaching the TRN-2000 to a glass surface

OMS-2000 Omni Speaker is used with the ANG-2200 to project acoustic noise into drop ceiling air spaces, closets, crawl spaces, and air ducts.

Laser Mic Surveillance Defeater Laser Countermeasure Surveillance Protection Device
STATEMENT OF WORK
1. A Privacy Protection Audit will be performed at the designated location. The purpose of the audit is to identify any physical, procedural and electronic / mechanical threats which would convey the transmission of audible, visual information from within the protected areas.
2. The service shall be provided during the time frames designated by the client and conducted in a confidential and low profile posture.
3. The technicians performing the service shall have extensive training and experience in the field, which shall be documented to the client’s satisfaction.
4. The equipment utilized is professional laboratory grade instrumentation. The technician performing the audit will be certified/ experienced in the operation of the following equipment:
- Radio Frequency Spectrum Analysis (100 kHz to 24 GHz)
- Real Time Spectrum Analysis (100 kHz to 6 GHz)
- Differential RF Analysis (100 kHz to 5 GHz)
- Broad Band RF Analysis (100 kHz to 12 GHz)
- Examination of Current Carrier RF to telephone and electrical lines.
- Examination of Visible and Infrared spectrum for transmission.
- Excitation of Cellular Bands to detect GSM surveillance devices.
- Utilization of UV light to identify physical tampering.
- Non-Linear Junction Detection to identify covert technology.
- Thermal Infrared Imaging to identify covert surveillance devices.
- Laser Refraction to identify covert cameras.
- Advanced Telephone/Line Analysis
Analog/Digital/VOIP examination with audio demodulation.
Frequency Domain and NLJD features required for line analysis.
5. The service shall include a threat assessment in conjunction with a physical security analysis. The sweep will follow industry accepted protocols for the identification of covert surveillance technology.
6. A verbal report shall be given at the completion of each sweep. A comprehensive written report shall be submitted within five business days of completion.
Suggested Technology
Research Electronics OSCOR Blue Spectrum Analyzer
Tektronix RF Hawk Real Time Spectrum Analyzer
Audiotel Delta V Differential Detector
Research Electronics CPM-700 Executive Kit Broad Band Receiver
Research Electronics TALAN Advanced Telephone Analyzer
FLIR Scout Thermal Imaging Camera
Research Electronics ORION NLJD
Air Magnet LAN / Wi-Fi Suites
TSCM Antenna Kit
Cell Phone Detection Kit
UV Lamp
Families of Bugs:
| Free Space Emission |
| Acoustic/Audible Pressure Waves |
| Acoustic/Ultrasonic Pressure Waves |
| Optical/Invisible Light (UV, etc…) |
| Optical/Visible Light |
| Optical/Invisible Light (Infrared, etc…) |
| RF Transmission (VLF) 3 kHz – 3 MHz |
| RF Transmission (HF) 100 kHz – 70 MHz |
| RF Transmission (VHF) 30 MHz – 300 MHz |
| RF Transmission (UHF) 300 MHz – 1 GHz |
| RF Transmission (Microwave Low) 900 MHz – 3 GHz |
| RF Transmission (Microwave Mid) 3 GHz – 12.5 GHz |
| RF Transmission (Microwave High) 12.5 GHz – 26.5/33/40 GHz |
| RF Transmission (Microwave mm) 26.5/33/40 GHz – 325 GHz |
| RF Transmission (Microwave mm2) 325 GHz – 1.5 THz |
| Free Space – Magnetic |
| Conducted Emission: |
| Audible (Voice Frequency) |
| Ultrasonic |
| Video |
| Current Carrier up to 500 kHz (AC Mains, Phone, CATV, etc.) |
| Radio Frequency (AC/Mains Devices, waveguide, etc.) |
| Fiber Optic |
Written by Darren L. Epstein, all rights reserved. Copyright © 2019 / (DO NOT COPY)

Thanks for the suggestion to use a TSCM device that can locate transmitters that are turned off or hidden within walls. My husband and I are thinking of opening our own business, but it would deal with a lot of confidential information from clients so we want to be sure to protect their information as best as possible. We’ll have to look into different TSCM options and services in our area!
Happy to help and good luck with your new business. If you ever need our assistance, world-wide… just let me know. We often handle TSCM and phone forensics together and can fly to your location. If you haven’t read an article we wrote on TSCM, take a look it might answer some questions. You can find it under “News & Events” within our websites top menu links, look for – COUNTERMEASURES… DEBUGGING SPYING DEVICES.
Ι simply couldn’t depart youг web site befоre saying that I extremely enjoyed tһe blog infoгmation. Itѕ going to be a site I check out for neԝ posts. Thanks, nice job
This blog COUNTERMEASURES… Debugging Spying Devices helped me a lot. Thank you!
Hi there friends, good article and pleasant arguments, I am genuinely enjoying!!
Way cool! Some extremely valid points! I appreciate you writing this article plus the rest of the site is very good.
Thanks to my father who informed me on the topic of this weblog, this blog is really amazing.
I like the helpful information you provide in your articles.
I will bookmark your blog and check again here regularly.
I’m quite sure I will learn a lot of new stuff right here!
Best of luck for the next!
I have recently started a web site, the information you provide on this website has helped me greatly. Thanks for all of your time & work.
Wow, superb blog layout! How long have you been blogging for?
you made blogging look easy. The overall look of your web
site is fantastic, let alone the content!
Thanks a lot for sharing this with all of us you really recognize what
you’re speaking about! Bookmarked. Please also
visit my site =). We may have a hyperlink alternate contract between us
Thanks a lot for sharing this with all of us you really realize what
you’re speaking about! Bookmarked. Kindly additionally talk over with my site =).
We can have a link exchange arrangement between us
Please help. I’ve been under surveillance for I feel around 7 months. Can you help me find someone in Fort Worth, Texas? It’s been horrible. I found things in my home, in my car (very well wired to look accurate), cell phones and all things electronic attacked. So much that people didn’t believe me. I have made multiple police reports but it still continues.
It would be our pleasure to assist you. Please contact us off the blog, go to the contact us section of our website and email your contact details and what you have been experiencing. Feel free to include photos if you have. We conduct TSCM (bug sweeps) worldwide, so not to worry you’re in Fort Worth TX. When you email us, we will respond with our direction approach, rates, and what you can expect. We also have the ability to leave equipment behind to assist you with hedging against electronic attacks. This is not crazy for us… rather the norm and we will believe you and take the situation seriously. NOTE: Continue contacting the Police Department, and OBTAIN POLICE REPORTS of the incidents you report, as many as you can… documentation is very important. Best to you and stay safe!
Great blog you have got here.. It’s hard to find good quality writing like yours these days.
I truly appreciate individuals like you! Take care!!
You are so cool! I don’t suppose I’ve read through a single thing like this before. So wonderful to discover somebody with a few unique thoughts on this subject matter. Really.. thank you for starting this up. This site is one thing that is required on the internet, someone with a bit of originality!
This is a really good tip particularly to those new to the blogosphere. Simple but very precise information… Many thanks for sharing this one. A must read post!
May I just say what a relief to find an individual who genuinely understands what they are discussing on the internet. You certainly understand how to bring an issue to light and make it important. A lot more people really need to check this out and understand this side of your story. I can’t believe you’re not more popular because you definitely have the gift.
Excellent web site you have here.. It’s difficult to find quality writing like yours these days. I truly appreciate individuals like you! Take care!!
That is the precise weblog for anybody who needs to search out out about this topic. You understand so much its nearly onerous to argue with you (not that I actually would need匟aHa). You positively put a new spin on a topic thats been written about for years. Great stuff, just great!
Thanks for sharing, this is a fantastic blog. Keep writing.
Youre so cool! I dont suppose Ive learn something like this before. So good to find any individual with some unique thoughts on this subject. realy thanks for starting this up. this website is one thing that’s needed on the web, somebody with a bit originality. helpful job for bringing something new to the web!
Good post. I will be dealing with some of these issues as well..
I needed to thank you for this excellent read!!
I definitely enjoyed every little bit of it. I have got
you book-marked to check out new stuff you post…
I simply could not leave your website before suggesting that
I actually loved the standard information a person supply for your guests?
Is going to be back frequently to check up on new posts
Excellednt post. I certainly love this website.
Thanks!
I constantly spent my half an hour to read this web site’s posts everyday along with a mug of coffee.|